Let's take a look at how to Enable/Disable TLS 1.2 in Windows Server using the IISCrypto tool. I will also show how to test TLS 1.2 using some clients like Web Browser Firefox and IE.
What is IIS Crypto ?
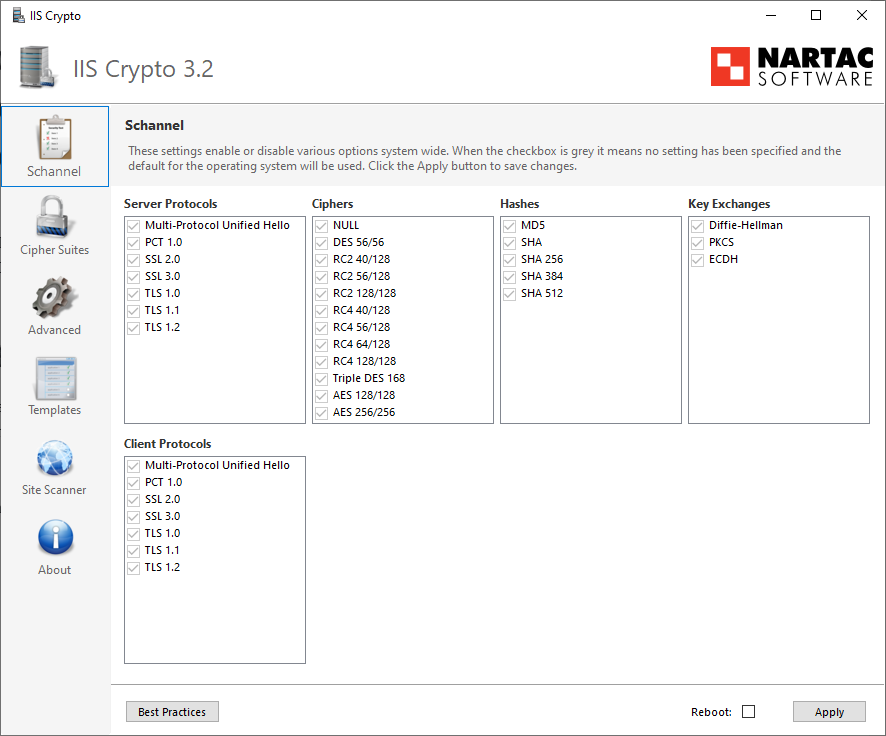
IIS Crypto is a free tool used to enable or disable protocols, ciphers, hashes, and key exchange algorithms on Windows Server 2008, 2012, 2016, and 2019. To download the free tool visit here (https://www.nartac.com/)
This tool is an executable file and can be used directly on the server, no need to install it.
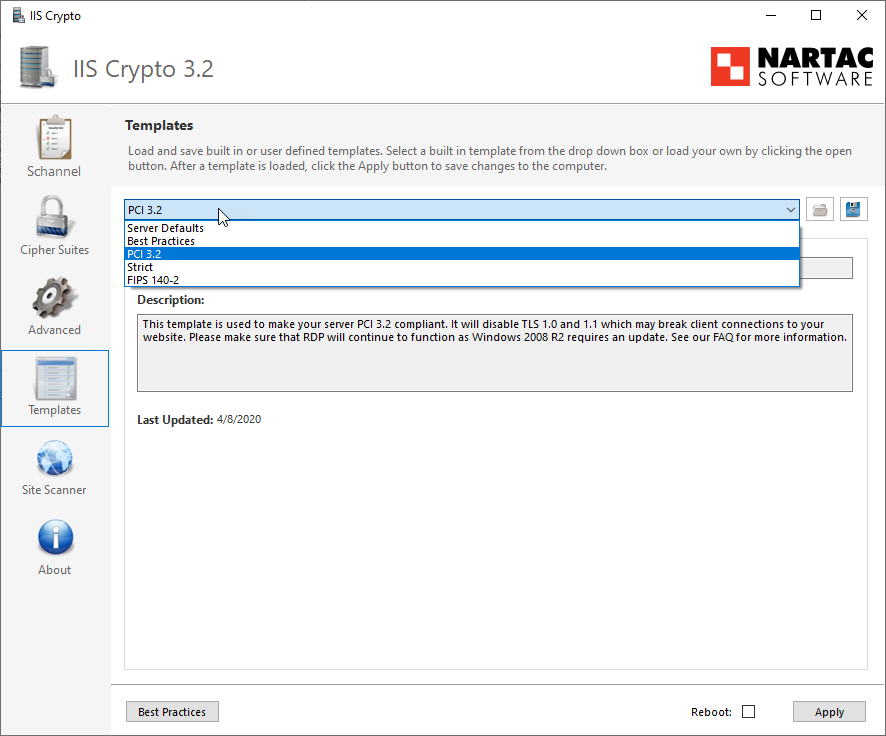
There are various template available which sets the required setting for you. Best template to choose is PCI 3.2
This template is used to make your server PCI 3.2 compliant. It will disable TLS 1.0 and 1.1 which may break client connections to your website. Please make sure that RDP will continue to function as Windows 2008 R2 requires an update. See our FAQ for more information.
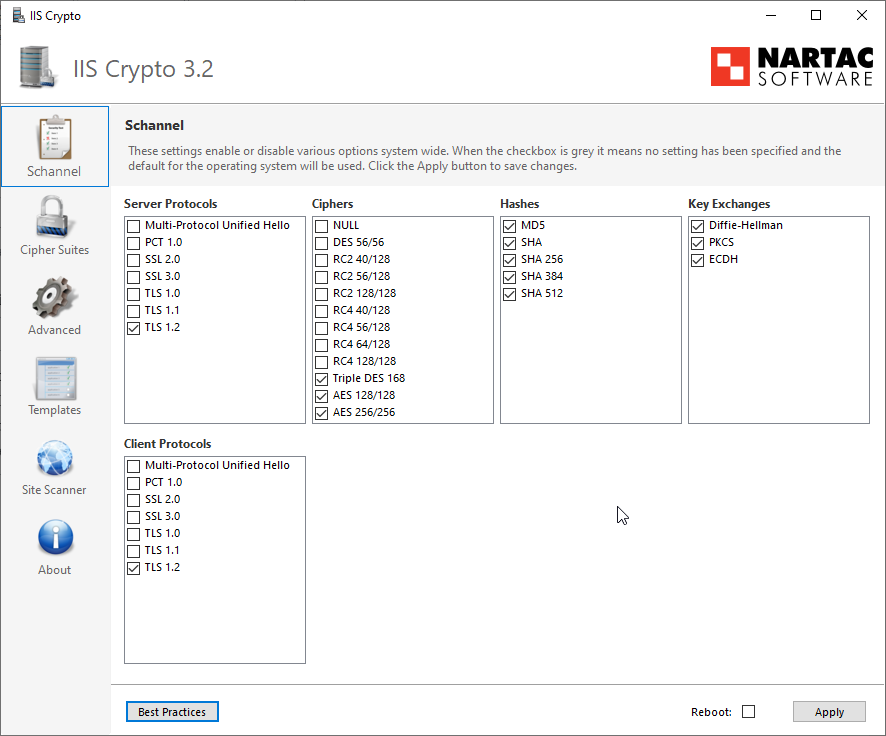
Click on Apply and reboot the server to apply the changes.
Now changes are done in the web server, how to validate whether the changes made are working as expected?
Short Video of this implementation
Verify TLS changes using Web Browser
FireFox
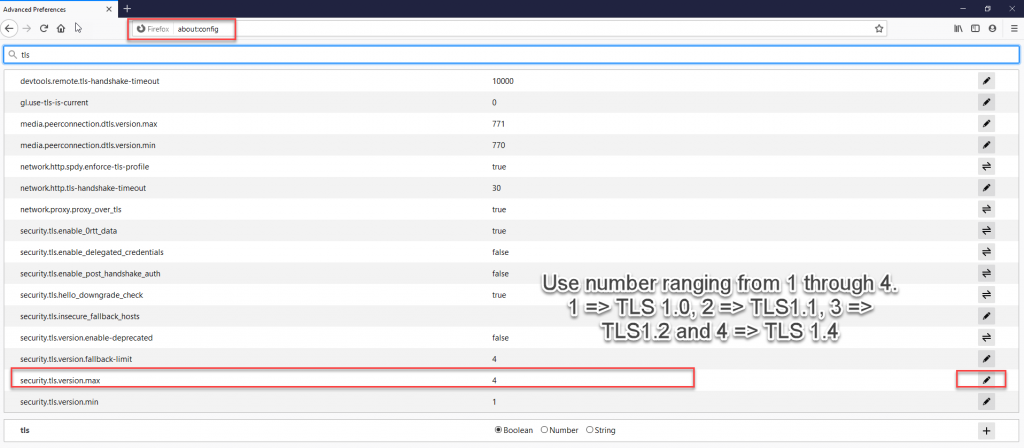
- Open Firefox
- In the address bar, type about:config and press Enter
- In the Search field, enter TLS. Find and double-click the entry for security.tls.version.max
- Set the integer value to 4 to force a maximum protocol of TLS 1.3.
Microsoft Internet Explorer
- Open Internet Explorer
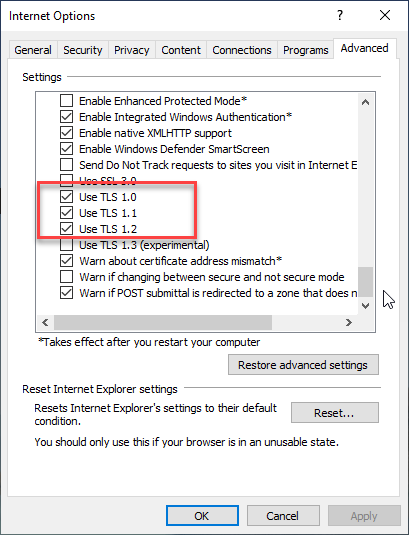
- From the menu bar, click Tools > Internet Options > Advanced tab
- Scroll down to Security category, manually check the option box for Use TLS 1.1 and Use TLS 1.2
- Click OK
- Close your browser and restart Internet Explorer
Google Chrome
Connections are automatically negotiated at the highest grade.
If you are using Google Chrome version 22 or greater, TLS 1.1 is automatically supported. TLS 1.1 & 1.2 are automatically enabled from version 29 onwards
Once you make required changes in the browser, E.g. enable TLS 1.0 alone, your web server should now reject the call. This concludes that the web server now supports only TLS 1.2 and not lower versions.
Related Post
You might be interested in the below security-related post, take a look.
- How to remove the server header from ASP.NET Core 3.1
- How to apply various Security Feature in ASP.NET Core application
Conclusion
In this post, I showed How to Enable/Disable TLS 1.0, 1.1, and 1.2 in Windows Server using the IISCrypto tool. If you have any questions or just want to chat with me, feel free to leave a comment below.
